here is link http://ctf.infosecinstitute.com/levelone.php
1#> level one is so easy just view source code and top line ##<!-- infosec_flagis_welcome -->
2# > the image is looks like broken but its not, Check source code
this is the image save as using #linux wget command wget http://ctf.infosecinstitute.com/img/leveltwo.jpeg image must be contain flag lets check linux command # strings leveltwo.jpeg we got base64 aW5mb3NlY19mbGFnaXNfd2VhcmVqdXN0c3RhcnRpbmc=
decode ## infosec_flagis_wearejuststarting
3#> QR code is morse code decode ##INFOSECFLAGISMORSING
4#>
using burfsuite view http traffic history here is some interesting cookie text vasbfrp_syntvf_jrybirpbbxvrf lets decode cieser ##infosec_flagis_welovecookies Cieser decrypt used site https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript
5#> first when we logging level five page you will see
stop script clicked and then
this image will show lets check this image using steghide tool
#steghide --info alies.
lets extract all.txt file #steghide extract -sf aliens.jpg -xf all.txt
convert binary to text ##infosec_flagis_stegaliens
6#> Do you want to download sharkfin.pcap file?
packets are nothing special but if we see first line UDP packet
convert hext to ascii ## infosec_flagis_sniffed
7#> f00 not found Something is not right here??? btw...bounty $70
if we see link http://ctf.infosecinstitute.com/404.php link was always levelone _ leveltwo like that lets change link http://ctf.infosecinstitute.com/leveleleven.php in gif and phplogo image nothing then we checked using burfsuite http packet cookie
if we see cookie fusrodah=vasbfrp_syntvf_jrybirpbbxvrf ==> convert ROT13 ## infosec_flagis_welovecooki
8#> This flag was so easy
## infosec_flagis_0x1a
9#> we need Cisco IDS default passwords https://portforward.com/router-password/ one by one check --> ‘root’/’attack’ is worked
Linux command using reverse echo "ssaptluafed_sigalf_cesofni" | rev
## infosec_flagis_defaultpass
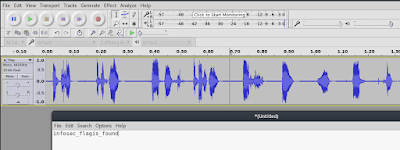
10#> sound file open by Audacity program set play back speed 12 then you will listing flag
11#> download php-logo-virus.jpg type #strings strings php-logo-virus.jpg | grep flag
12#> noting in image so lets click ctrl+u source code if we open design.css file
13#> :Description WHAT THE HECK HAPPENED HERE? IT SEEMS THAT THE CHALLENGE HERE IS GONE?
CAN YOU FIND IT? CAN YOU CHECK IF YOU CAN FIND THE BACKUP FILE FOR THIS
ONE? I’M SORRY FOR MESSING UP :(
little bit tested directory after found levelthirteen.php.old open source code then you will find
/* <img src="img/clippy1.jpg" class="imahe" /> <br /> <br />
<p>Do you want to download this mysterious file?</p>
<a href="misc/imadecoy">
<button class="btn">Yes</button>
</a>
<a href="index.php">
<button class="btn">No</button>
</a>
*/
lets follow ctf.infosecinstitute.com/misc/imadecoy download pcap file
wireshark -> file export objects -> http > honyPY.png
14#>
Description: Do you want to download level14 file? http://ctf.infosecinstitute.com/misc/level14
-- Dumping data for table `flag?`
hex format let by pass \\u00 to a “space” char let convert it will hex :
lets convert hext to ascii http://www.yellowpipe.com/yis/tools/encrypter/index.php
## infosec_flagis_whatsorceryisthis
--------------------------------------------------------------
another way to find
The file provided for this level seems to be phpMyAdmin SQL Database Dump in ASCII. After some looking around I noticed the “friends” table had a stange entry under the name field for id 104. It’s Unicode encoded string. To convert it to ASCII, I used an online tool after googling for “Unicode to ASCII online”.
'\\u0069\\u006e\\u0066\\u006f\\u0073\\u0065\\u0063\\u005f\\u0066\\u006c\\u0061\\u0067\\u0069\\u0073\\u005f\\u0077\\u0068\\u0061\\u0074\\u0073\\u006f\\u0072\\u0063\\u0065\\u0072\\u0079\\u0069\\u0073\\u0074\\u0068\\u0069\\u0073'
$ echo '\\u0069\\u006e\\u0066\\u006f\\u0073\\u0065\\u0063\\u005f\\u0066\\u006c\\u0061\\u0067\\u0069\\u0073\\u005f\\u0077\\u0068\\u0061\\u0074\\u0073\\u006f\\u0072\\u0063\\u0065\\u0072\\u0079\\u0069\\u0073\\u0074\\u0068\\u0069\\u0073' | sed 's/\\u/\u/g'
\u0069\u006e\u0066\u006f\u0073\u0065\u0063\u005f\u0066\u006c\u0061\u0067\u0069\u0073\u005f\u0077\u0068\u0061\u0074\u0073\u006f\u0072\u0063\u0065\u0072\u0079\u0069\u0073\u0074\u0068\u0069\u0073$ python -c "print u'\u0069\u006e\u0066\u006f\u0073\u0065\u0063\u005f\u0066\u006c \u0061\u0067\u0069\u0073\u005f\u0077\u0068\u0061\u0074\u0073\u006f\u0072\u0063\u0065 \u0072\u0079\u0069\u0073\u0074\u0068\u0069\u0073'"
infosec_flagis_whatsorceryisthis -------------------------------------------------------------------- this level we can use dns tool for dns lookup , but It possible to run two command in one line by adding ; . For instance, we can show all file directory :
rndc.or.id;ls -la
it will show “.hey” file and index.php file ,
we even can show all user data with “rndc.or.id;cat /etc/passwd” that users with name “aurelius”, but already remove i think
if we do a command “rndc.or.id;cat .hey”
or direct access on http://ctf.infosecinstitute.com/levelfifteen/.hey
it will show another encrypt
Miux+mT6Kkcx+IhyMjTFnxT6KjAa+i6ZLibCwhat this encrypt ???
I finnaly Found the type encryption cause i try random decode on http://crypo.in.ua/tools for decode any encryption
it result : ATOM-128 encryption
so i just directly decode it on http://crypo.in.ua/tools/eng_atom128c.php
it will result a flag :infosec_flagis_rceatomized
FLAG : infosec_flagis_rceatomized


















No comments:
Post a Comment